Monday, May 18, 2009
WorkShop 7 End of the Line: Production Site Migration and Maintenance
Sunday, May 17, 2009
Workshop 6 Enjoying the Ride: Web framework Alternatives, Scalability and Flexibility
Saturday, May 16, 2009
Workshop 5 Admiring the scenery Forms, AJAX Screen Layout and Mobile Interfaces
Customer service. Web 2.0 platforms offer companies the ability to create very interactive high-quality customer service sites that network together customers, staff, and suppliers. In addition, companies can create customer service sites moderated by full-time employees that encourages end-user created content and wide participation among users—enhancing consumers’ customer service experience and building loyalty. ( BoozAllen, 2007)
- Didactic efficiency
- Technical feasibility
- Cost effectiveness

This new business process system performs a large number of measurements. The company has been able to identify savings by a reduction of the distance from vehicle to customer . Other benefits for taxi drivers are better information access, new services available and improved work environment. Customers experience reduced estimated time of arrival and faster reservation process. The traffic control office is able to perform real-time information retrieval from the cars and at the same time benefits from location based retrieval advantages, improved information retrieval from the mobile resources and finally, real time notification advantages are also achieved. (Heijden, 2002)
References:
1. BoozAllen, 2007, " Companies to adapt to Web. 20 "<http://www.boozallen.com/media/file/The_Urgent_Need_for_Companies_to_Adapt_to_Web_2.0.pdf>
2. Heijden, 2002, " Buisness Process"<http://is2.lse.ac.uk/asp/aspecis/20020043.pdf>
3. 2. Attewell, J., & Savill-Smith, C. (2005), ‘Mobile learning anytime everywhere: A book of papers from MLEARN 2004
<http://elearning.typepad.com/thelearnedman/mobile_learning/reports/mLearn04_papers.pdf>
Wednesday, May 13, 2009
Exercise 26: System Integration
- Assisting the organization to improve telesales, account, and sales management by optimizing information shared by multiple employees, and streamlining existing processes (for example, taking orders using mobile devices)
- Allowing the formation of individualized relationships with customers, with the aim of improving customer satisfaction and maximizing profits; identifying the most profitable customers and providing them the highest level of service.
- Providing employees with the information and processes necessary to know their customers, understand and identify customer needs and effectively build relationships between the company, its customer base, and distribution partners.
Tuesday, May 12, 2009
Exercise 25: M-commerce and the E-Wallet : Innovation and Mobile Devices
Exercise 24: Virtual Business Worlds and Cyberagents
- Intelligent Software Agent
- Autonomous Agent
- Distributed Agent
- Multi-agent System
- Mobile Agent
- Fuzzy Agent
2. Intelligent Software Agent and Fuzzy Agent would be applied to the Artificial Intellegience and while Statistical Techiques would use under Mobile Agent.
Sunday, May 10, 2009
Exercise 23: Searching Mechanisms
Exercise 22: CRM, B2B and SCM Software
Exercise 20: Modeling and UML

A. Class Diagram ( Jua, n.d.)

B. Case Diagram ( Jua, n.d.)
Saturday, May 9, 2009
Exercise 19: TP Monitors and Transaction Protocols
- Atomicity is related to the begin and end of transation statement, once is started just like an atomic and the work is done.
- Consistency preserves data stability and transform from one to another
- Isolation allows concurrency of transaction to behave as one of the transaction running under the system
- Durability is a unit of recovery
2. Transaction processing monitors have been evolving for about 30 years (CICS was introduced in 1968) and have become powerful, high-speed server platforms for mission-critical applications. Some TP products like CICS and TUXEDO. TP monitors are operating systems for business systems whose applications are written in languages like COBOL. It may seem strange to call a TP monitor an "operating system," but because they control an application's entire environment, it's a fitting description. TP monitor systems automatically manage the entire environment that a business system runs in, including transactions, resource management, and fault tolerance. The business logic in TP monitors is made up of procedural applications that are often accessed through network messaging or remote procedure calls (RPC), which are ancestors of RMI. Messaging allows a client to send a message directly to a TP monitor requesting that some application be run with certain parameters. It's similar in concept to the Java event model. Messaging can be synchronous or asynchronous, meaning that the sender may or may not be required to wait for a response. RPC is a distributed mechanism that allows clients to invoke procedures on applications in a TP monitor as if the procedure was executed locally. The primary difference between RPC and RMI is that RPC is used for procedure -based applications and RMI is used for distributed object systems. With RMI, methods can be invoked on a specific object identity, a specific business entity. In RPC, a client can call procedures on a specific type of application, but there is no concept of object identity. RMI is object oriented; RPC is procedural. (O' Reilly. 2001)
Example Show the TP Monitor Process (ETH Zuerich, n.d.)

3. RPC is a point to point protocol in the sense that it supports the interaction between two entities: the client and the server, when there are more entities interaction with each other ( a client with two servers, a client with a server and the server with a database), RPC treats the call as independent of each other. However, the calls are not independent. Transactional RPC is the additional language contstructs and run time support to bundle serveral RPC calls into an atomic unit Message Oriented Middleware (MOM) -products provide an assured, asyncronous and connectionless method to exchange messages between processes. (ETH Zuerich, n.d.)
Digaram shows the basic MOM:

4. One-phase atomic commit protocol can have the decision to abort the process in server, this will affect the stability and consistency of the transaction, however, two phase commit protocol involved in the client side as well in order to abort the transaction, therefore, it is more secure and consistency on the transaction process.
2.O' Reilly, 2001,"Transaction Processing Monitor "
<http://docstore.mik.ua/orelly/java-ent/ebeans/ch01_05.htm>
3. ETH Zuerich, n.d., " Example of TP Monitors"
<http://www.iks.inf.ethz.ch/education/ws05/eai/slides/lec3.pdf>
Exercise 18: Threading Demonstration in Python
Friday, May 8, 2009
Exercise 17: Concurrency Terms
Wednesday, May 6, 2009
Exercise 16: Authentication and Encryption Systems

2. VeriSign, Inc. is the trusted provider of Internet infrastructure services for the networked world. Billions of times each day, it provides SSL, identity and authentication, and domain name services allow companies and consumers all over the world to engage in trusted communications and commerce. It offers solution on SSL certificates, identity and authenication services, domain name services, code signing, internet defense network and enterprise security and communication services for e-commerce. (VeriSign, 2009).
Wednesday, April 29, 2009
Exercise 15: Protecting and Archiving Data
Exercise 14: Electronic Payments and Security II
References:
1. Wikipedia, 2009, ' Http Cookies'
<http://en.wikipedia.org/wiki/HTTP_cookie>
Exercise 13: Electronic Payments and Security
2. Secure Electronic Transactions (SET) is an open protocol which has the potential to emerge as a dominant force in the securing of electronic transactions. Jointly developed by Visa and MasterCard, in conjunction with leading computer vendors such as IBM, SET is an open standard for protecting the privacy, and ensuring the authenticity, of electronic transactions (IBM 1998). SET is comparatively secure common with SSL , since SET needs to have the additional software be installed and informed an other third party , however, SSL just only cater directly with customers and merchants only.SET is not common in the market, since the cost and additional software and configuration had to implemented. (Wikipedia, 2009)
References:
Wikipedia, 2009, ' Secure Socket Layer'
<http://en.wikipedia.org/wiki/Secure_socket_layer>
Saturday, April 25, 2009
Exercise 12: Designing for a Secure Framework
2. Network-based intrusion detection systems use raw network packets as the data source. A
network-based IDS typically utilizes a network adapter running in promiscuous mode to monitor
and analyze all traffic in real-time as it travels across the network. Its attack recognition module
uses four common techniques to recognize an attack signature:
· Pattern, expression or bytecode matching,
· Frequency or threshold crossing
· Correlation of lesser events
· Statistical anomaly detection
complex and interconnected as they are today. In this simpler environment, it was common
practice to review audit logs for suspicious activity. Intrusions were sufficiently rare that after the fact analysis proved adequate to prevent future attacks (ISS, 1998)
Sunday, April 12, 2009
Workshop 4- Riding the Rails with Ruby
2. The difference between Javascript and Ruby (Githud, 2008)
Ruby:
def create
@milestone = Milestone.new @params['milestone']
@milestone.creator = @person
@milestone.domain = @person.domain
if milestone.save
flash['notice'] = 'Milestone ' + @milestone.name + ' is created.'
redirect_to_action 'show', :id => @milestone.id
else
render_action 'new'
end
Javascript:
this.create = function(req, res) {
with (res) {
res.milestone = Milestone.newInstance(req['milestone']);
milestone.creator_id = person.id;
milestone.domain_id = person.domain_id;
if (milestone.save()) {
flash['notice'] = 'Milestone ' + milestone.name + ' is created.';
redirectToAction('show', milestone.id);
} else
renderAction('newInstance');
}
}
-Ruby use elsif and else whereas , javascript use elseif and else
- Javascript use open bracket for conditions () and {} whereas Ruby didn't use that
Challenge Problem

2. FizzBuzz Source
FizzBuzz Result
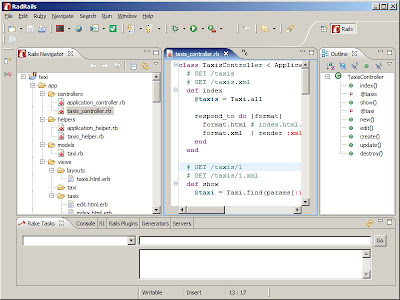
Workshop 3 Online Taxi Booking System
1. Setup the MySQL Tools
a: MySQL Query Browser with the inserted records and result

b. MySQL Administrator Tool with table properties added

c. MySQL Administrator creatd the database: itc and table : passsengers
# Warning: The database defined as "test" will be erased and# re-generated from your development database when you run "rake".# Do not set this db to the same as development or production.
production:
Workshop 2- Model View Controller design approach
1. Join one of the classmates , Dennis focus group to take parts in the discussion.
2. A web application framework is a software framework that is made to support the development of dynamic websites, web application and web services ( Wikipedia, 2009). Ruby on Rails provides beautiful code by convention over configuration and it has taken the programming world by storm by its MVC approach to application developement. Also, it provides a micro-framework weighing 4kb, therefore, it keeps things simple and minimal dependencies ( Mindtree, 2008)
3.a.The "topic does not exist yet " under the web page
3.b. MVC is firstly developed by Trygve Reenskaug in year 1979. As Model View Controller has their own responsibility, for instance, stores the data and application logic for the interface . View is used to renders the interface (usually to the screen) . Model is Responds to user input by modifying the model .
4. UC Berkeley RAD lab’s Ruby on Rails Short course is an interesting presentation.
5. The article is concerning the approach and the responsibility of the MVC
Challenge Problem:
1. The controller is used to maitain the index, new, edit , create, and delete. It can be created by generating under the RadRails
2. View is used to handle the view of new, index, show and edit.erb and the extention can change to rhtml in order for Rails to read on them.
Wednesday, April 8, 2009
Workshop 1 - Setting up the model railway
a. Table of Passenger_destination

b. Table of Passenger_orgin

To Do:
1. From the “Learning Rails” podcasts, I just chose the topics which were aroused my interests only :-)
2. Ruby on Rails is installed in my notebook

3. Yes, Instant Rails is using, therefore, save the time on configuration.
Challenge Problem
1. I did not do much programming over my career path even, when I was in school. Therefore, the programming languages i know just only a few:
a. javascript
b. java
c. html
4. Rails has sensible defaults for every aspect of a web application. Following the conventions, you can write a Rails application, using less code than most other web application frameworks. If you need to override the conventions, it's also easy with Rails. Taking advantage of the built-in defaults of the Rails framework has a wide range of advantages over making up your own. One of the biggest is that it makes it easier for other programmers to understand your code. (Wiki, 2009)
# compute pi
end
compute_pi() => 3.14...
compute_pi(2) => 3.1
The convention is that you compute pi upto 10 decimals. This will be enough for most uses, but you can override it if you want.Such small-scale convention over configuration is also valuable in existing projects. (Jacobs, 2006)
- Adding a new way to examine data is simply a matter of adding a new view. Often no change to the model is necessary, nor is it necessary to change other views!
Wednesday, April 1, 2009
Exercise 11: XML Introduction
Saturday, March 28, 2009
Exercises 10: Application Server Platform in E-Commerce
- an online store
- conduct business to business or business(B2B) to consumer transactions(B2C)
- mobile commerce
Comparsion between DB2 and MySQL (IBM, 2006)

Oracle has provide an Oracle iStore for E-commerce solution. This product is using Oracle as a database. It offers the features and benefits: (Oracle, 2009)
- It builds, manage and personalize powerful, global and scalable internet storefronts.
- Istore supports both business to buisness (B2B) and business to customer (B2C) selling models
- Lower the cost of sales and improve services with an online commerical presence.
Compare betweem Oracle and MySQL(Petri, n.d.)

Exercise 9: Web Form Design and Processing: A Basis for E-Commerce Interaction


Wednesday, March 25, 2009
Exercise 6: Some Server Practice with PHP

b. $Server_Name

c. $PHP_Self

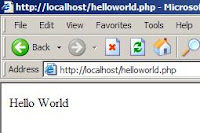
2. Helloworld.php